Multifactor authentication (MFA) might no longer be enough to protect your accounts
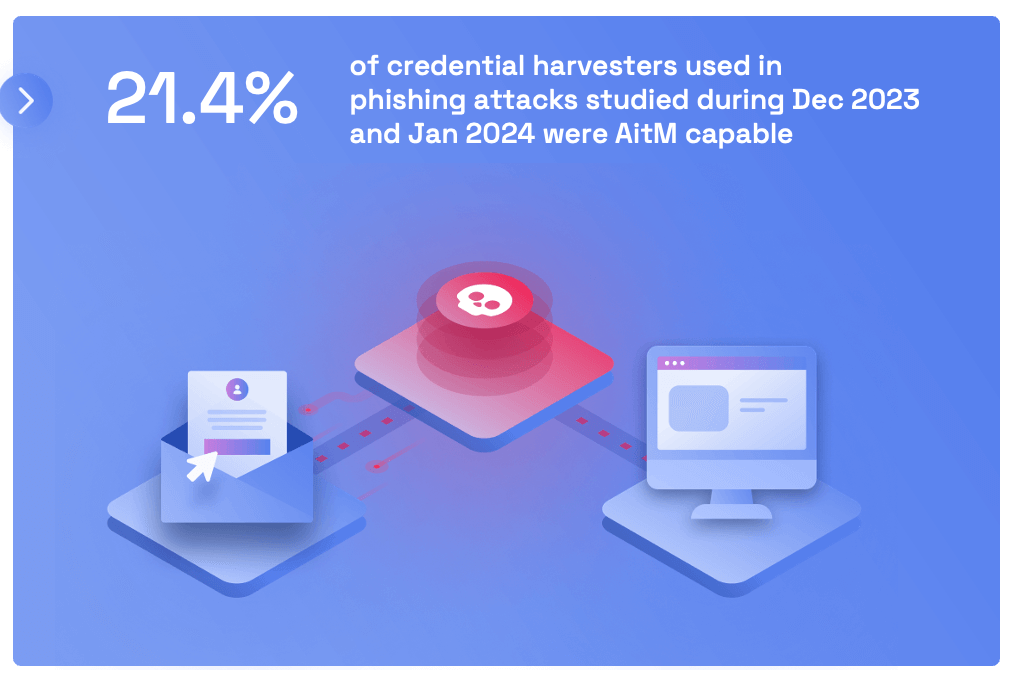
Credential harvesting happens when cyber attackers capture user credentials through websites that mimic login screens or forms. It has been a common strategy for hackers for some years now. Multifactor authentication has been widely accepted as a suitable method for de-escalating attacks like this. However, our latest research shows that hackers increasingly harvest MFA and session tokens.
Instead of verifying their session on their device, phishing victims unknowingly log in to the hacker’s device. When prompted to authenticate through MFA, the victim thinks they're logging into a legitimate service and accepts the request.
And there – the hacker now has access to the account.
While multifactor authentication is still recommended cybersecurity practice, it might no longer be the silver bullet it used to be.
Adversary-in-the-Middle (AiTM) and other phishing trends
The technique described above is called the Adversary-in-the-Middle (AiTM) credential harvester. It's one of the advanced and alarming phishing techniques explored in Hoxhunt’s Q4 Threat Intelligence Report.
Additionally, the report covers some of the emerging risks associated with social media and AI. We also discuss trending phishing techniques and social engineering tactics observed in the Hoxhunt network.
We created the report to illustrate the current threat landscape. We aim to allow organizations and individuals to stay one step ahead of threat actors and mitigate risk.
Download the full report by submitting your details below.

About the authors
Hoxhunt’s Threat Operations Team consists of threat analysts and data scientists tasked with handling the emails reported to Hoxhunt.
During Q4 2023, around one million email threats were reported by our end users, averaging almost 10,000 reports per day. Because our end users manually report the emails, our data only consists of threats that have managed to bypass email spam filters. This data is analyzed by the Threat Operations team and combined with other data sources to create actionable intelligence.






