Total costs of phishing
The 2023 IBM / Ponemon Cost of a Data Breach Report puts the average global cost of data breaches due to phishing at $4.76 million. Social engineers are targeting employees with increasingly sophisticated phishing attacks and increasingly often--SlashNext Inc. discovered a 1,265% increase in phishing attacks in 2023--in the age of generative AI.
Bottom line is, phishing takes a major toll. But there’s hope. A well-trained workforce is, according to IBM / Ponemon, able to cut the costs of phishing down by half according to the 2021 Ponemon Cost of Phishing report; employee training is a top-3 “cost-mitigating factor” of data breach costs, according to the 2023 IBM report.

Phishing is a people-targeted online attack, traditionally via email. But today, social engineers can reach out and trick someone through all sorts of vectors. The direct costs of phishing and their share of the data breach pie chart may be bigger than is typically depicted due to how researchers are slicing the phish-pie.
The IBM / Ponemon report separates the below types of breaches into categories --with associated costs, incidence, and time to detect and contain--that we’d suggest basically comes back to social engineering and a phishing attack or something similar, i.e. fraudulent SMS, Slack or Teams messages.
Time, money, and frequency of phishing / social engineering

The sources of data breaches highlighted above and listed below are all people-targeted attacks. They typically contain a phishing element and together comprise 47.5% of all breaches.
- Phishing: $4.76M | 16% of all breaches | 293 days to identify and contain
- Stolen or compromised credentials: $4.62M | 15% of all breaches | 328 days to identify and contain
- BEC: $4.67 M | 8.5% of all breaches | 266 days to identify and contain
- Social engineering $4.55 | 8% of all breaches | 298 days to identify and contain
1. Business Email Compromise (BEC) and phishing
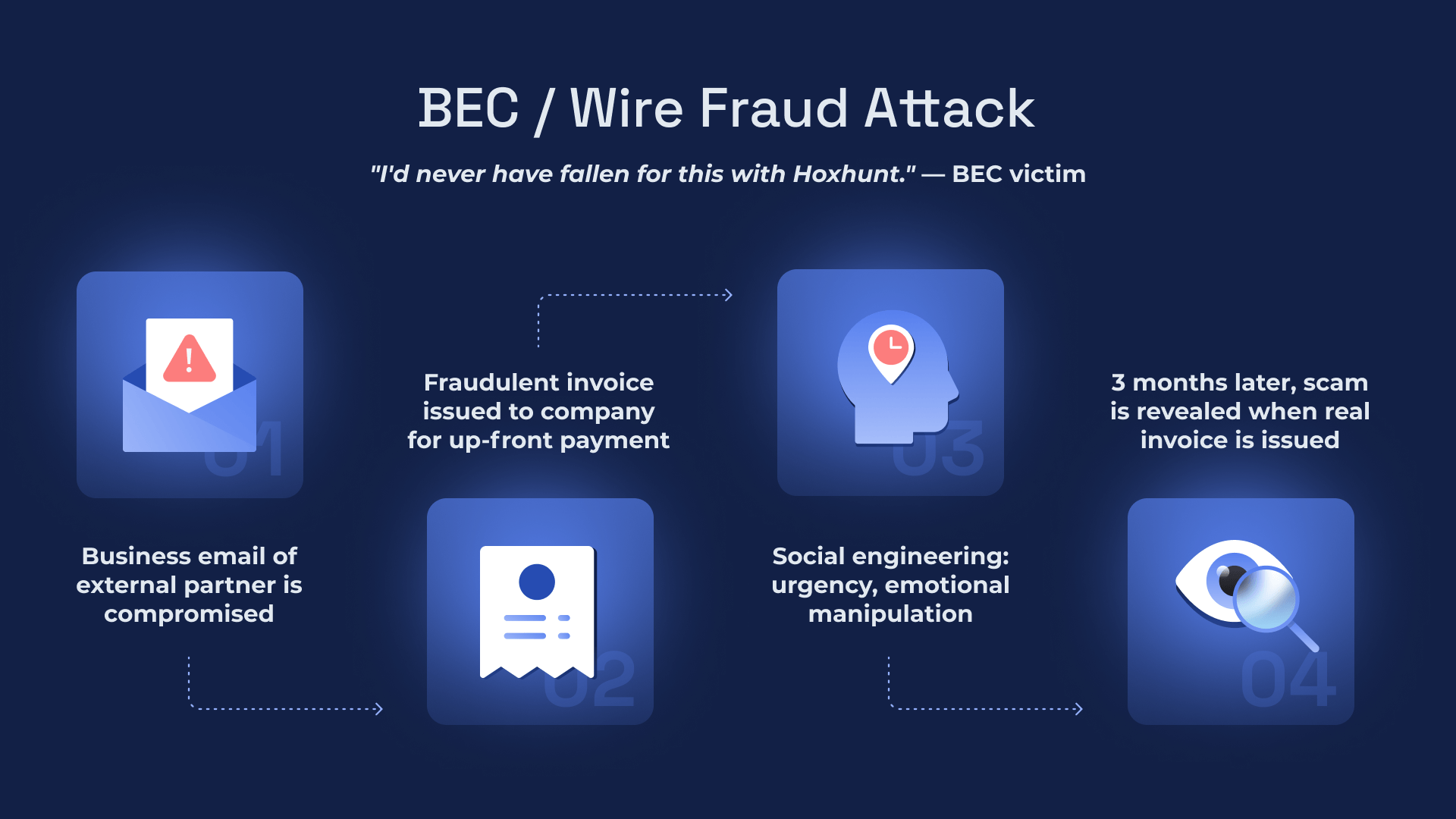
The FBI reports that BEC is the most prolific and costly form of cybercrime. According to the FBI’s most recent IC3 report, businesses lost more than $2.7 billion to BEC attacks, $300 million more than in 2021. It's important to note that these are reported losses, and the vast majority go unreported.
BEC is also known as Email Account Compromise, Wire Transfer Fraud, and CXO or CEO Fraud because the scam begins with someone hijacking an email account and posing as the CXO, and ends with a lot of money being redirected to a hacker’s account. The target can be anyone at the executive level. It’s hit private individuals, governments, companies, and celebrities alike.
At $121 million, Facebook and Google were hit with the biggest loss from BEC ever back in 2015 in a criminal scheme that involved fake invoices from an impersonated company.
The 2023 IBM / Ponemon study reports that BEC breaches cost on average $4.67 million and take 266 days to detect before being contained. Time is money when it comes to detection: breaches that are contained in more than 200 days cost $1.02 million more than those contained in under 200 days, according to the same report.
Using different criteria, the Ponemon Institute reported in their Cost of Phishing study in 2021 that the average cost of BEC was $5.96 million, with maximum losses topping $8.12 million.
The 2023 Verizon DBIR reaffirmed BEC’s position as the king of cybercrime. Social engineering was the primary attack vector for 74% of all data breaches, but the incidence of BEC, or what they also call pretexting, doubled over the previous year. The Verizon DBIR noted that global companies with distributed workforces are particularly at risk.
Learn how Wateraid stopped BEC attacks

2. Ransomware and phishing
Turns out, just because ransomware is still a plague on information security even if itsn’t in the headlines as much as during the pandemic. According to IBM / Ponemon, the $5.13 million average cost of a ransomware attack in the 2023 report increased 13% from from $4.54 million in 2022. While ransom demands have fallen, attacks have increased. As an Oct. 17 article in the Wall Street Journal reported, ransomware came back in a big way in 2023. The article contained some shocking numbers:
- Chainalysis said victims will pay hackers around $900 million by the end of 2023, up from $457 million in 2022, despite generally lower rates at which victims do pay ransoms.
- Cyber insurer Coalition said claims reached record highs, with the average loss at around $365,000 in the first half of 2023, compared with around $227,000 for the previous six months; ransomware claims frequency rose by 27% across its policyholders in the first half of the year, from the second half of 2022.
- Resilience Cyber Insurance (who raised $100M Series D announced in Aug. 2023) reported that: 16.2% of its total claims were related to ransomware; there was a 1,100% increase in ransomware incident notifications between the second quarters of 2022 and 2023; and that notices received so far this year have already reached 100% of those in 2022.
- Cyber insurer Corvus said that the number of victims that hackers posted to leak sites on the darknet increased by 79.8% year over year

Ransomware is a form of malware that encrypts data in computer systems until a ransom is paid for an encryption key that will unlock them for data retrieval or re-starting operations. Most ransomware breaches begin with a phishing email.
Big players pay big bucks to get their systems back. The highest payout on record is $40 million by a Chicago-based insurance company in 2021, “the year of ransomware,” when Colonial Pipeline paid 75 bitcoin, or $4.4 million to get its oil distribution back online, and JBS paid $11 million to resolve an attack that halted operations for the largest meat producer in America (more on the cost of operational downtime later).
3. Credential compromises and phishing
In phishing, credential compromise occurs when someone clicks on a link and is redirected to a malicious credential harvesting site. Credential harvesters trick people into entering sensitive data, such as passwords and account numbers. The Ponemon Institute reports that the average costs of credential compromises more than doubled to $2.1 million between 2015 and 2021. These attacks are simple to execute and cheap to purchase online via phishing kits.
According to IBM, compromised credentials:
- Were the second most common entry point for cyber attackers at 15% of all breaches, behind “Phishing” at 16%.
- Cost $4.62 million on average, second to phishing at $4.76 million.
- Take 11 months on average for security teams to detect and contain, 2 months longer than the average data breach.
4. Malware fuels phishing
The average total cost to resolve (non-ransomware) malware attacks was $807,506 in 2021, more than doubling 2015’s $338,098, according to Ponemon. Costs from uncontained malware increased from an average of $3.1 million to $5.3 million.
Malware comes in all shapes and sizes, and even the really simple forms can have complex global effects. Hoxhunt CEO and co-founder, Mika Aalto commented on research that was reported in Security Boulevard that 80% of incidents tracked by ReliaQuest in 2023 were from three versatile malware loaders, one of which has been making the rounds since 2007: QakBot (30%), SecGholish (27%) and Raspberry Robin (23%).
[.c-quote-box][.c-quote-wrapper][.c-quote-icon][.c-quote-icon][.c-quote-right-col][.c-quote-text-wrapper][.c-quote-text]Most email attacks are the product of phishing and malware kits purchased for peanuts off the dark web, so black hat tools with a proven track record and a cheap price tag will continue to dominate,” Aalto told Security Boulevard. “Recent advances in black hat generative AI, like FraudGPT, are still more pricey, more complicated, and more resource-intensive to use, so tools like malware loaders remain attractive for the scattershot mass-email-attack approach.[.c-quote-text][.c-quote-text-wrapper][.c-quote-name-wrapper][.c-quote-name]Mika Aalto, co-Founder and CEO of Hoxhunt[.c-quote-name][.c-quote-name-wrapper][.c-quote-right-col][.c-quote-wrapper][.c-quote-box]
5. Employee productivity, mental health & operational downtime
The cost of lost productivity due to a phishing attack ballooned from $1.8 million in 2015 to $3.2 million per company in 2021, according to Ponemon. Social engineers target employees with their phishing attacks, so employees feel the effects of an attack when they need to see IT security about an incident. (Some people lose even more productivity by being forced into a corporate punishment like extra training and a phishing jail).
People can lose sleep, confidence, focus, and even their jobs over an email breach. The consumer group, Which? calculated total wellbeing cost due to fraud, much of which the study acknowledged stemmed from online attacks, at $12.26 billion (the UK study reported 9.3 billion GBP).
A 2014 Gartner study projected the average cost of operational downtime to be $5,600 per minute.
6. Phishing breaches lower share price
According to the Harvard Business Review: Publicly traded companies lost 7.5% in their stock values after a data breach, coupled with a mean market cap loss of $5.4 billion. It took 46 days, on average, for these companies to recover their stock prices to pre-breach levels, if they were able to do so at all. The HBR piece also notes that:
- 60% of organizations that have experienced data breaches have raised their product prices, so customers also feel the loss, not just shareholders.
- On average, companies experiencing a significant data breach incident underperform the NASDAQ by 8.6% after one year, and this gap can widen to 11.9% after two years.
7. Lost customers, brand damage and PR
The financial impact of losing customers and consumer trust can be anywhere from bad to catastrophic, particularly in industries where sensitive data is routinely handled, such as banking and healthcare. Companies spend significant sums to repair their image and convince their customers that it’s safe to do business with them.
8. Legal and regulatory
Legal and liability costs for breaches were arguably the top story in cybersecurity in 2023. The SEC introduced new data breach disclosure guidelines that shook up the industry with a federal lawsuit against Solar Winds and their CISO, Timothy Brown, on Halloween of 2023 for improper reporting of the legendary 2019 data breach, which began with a phishing attack.
Regulatory fines are escalating, and disclosure rules are becoming increasingly tight with other new regulations like Europe’s NIS 2 on the way.
Companies have four days to report a breach to the SEC once the breach has been determined to be material. With so many breaches beginning with a phishing attack, it’s vital to be able to detect and respond to breaches as quickly as possible to pinpoint when the attack started, and avoid getting hit with severe penalties.
Legal costs surrounding a breach include:
- Advice on disclosures
- Litigation
- Settlements: these can range from the hundreds of millions paid out since 2019 by each of Equifax ($575 million), Uber, and Facebook, on to the $875 million paid out by Amazon and the $1.19 billion that Chinese ride-hailing firm Didi paid out
- Indemnification: You might be on the hook for incident response costs by partners along the software supply chain who have been impacted by a breach of your system
Billable hours could range from the dozens to thousands to solve a lawsuit or regulatory dispute, at a clip of hundreds to over a thousand dollars/hour. Regulatory penalties, meanwhile, can be especially stiff in certain industries like healthcare.
And in a nightmarish turn that would be funny if it weren’t so scary, ransomware actors are using fear of the SEC to exact their pounds of flesh. In November of 2023, the ransomware gang, BlackCat filed a lawsuit to the SEC against a company, MeridianLink, who refused to pay them even after BlackCat threatened to report them.
9. Cyber insurance
Cyber insurance premiums keep rising, but thankfully they are no longer skyrocketing. Most blame ransomware for pushing the industry to the brink of collapse from 2020 to 2022, as premiums doubled and coverage shrank while ransomware payouts went through the roof. Insurers struggled to cope with the rising frequency and severity of claims as ransomware demands and payouts soared into the tens of millions, and reinsurers hid for cover.
Regulators worried that cyber insurance was incentivizing or enabling ransom payments with a “just pay 'em” attitude. The market saw a dramatic increase in premiums, a significant decrease in coverage, and a decline in profitability.
The National Association of Insurance Commissioners (NAIC) reported a 50% increase in US cyber insurance premiums in 2022, totaling $7.22 billion, according to Aon’s U.S. Cyber Market Update. Things have stabilized between 2022 and 2023. This Nov. 2022 article in the WSJ summarizes the 2022 rollercoaster ride from collapse to relative stability..
And then there’s the expansive and hard-to-interpret “cyber war exlcusion clause.” After kinetic and cyber war broke out in Ukraine, many insurers stopped covering cyber attacks that could be connected to a cyber war or a state-sponsored group or attack.
Cyber insurance trends
- Exponential growth: the cyber insurance industry wrote $600.000 in premiums in 2016 and $10 billion in premiums in 2021
- In 2019, the average cyber insurance premium in the U.S. was USD 1,500.
- In 2020, the average cyber insurance premium in the U.S. increased by 92% year over year, reaching USD 2,700.
- In 2021, the average cyber insurance premium in the U.S. increased by 73% year over year, reaching USD 4,300.
- In 2022, the average cyber insurance premium in the U.S. increased by 79% quarter over quarter, reaching USD 5,400.
- In 2023, premiums in Q1 “only” rose by 11%, compared to 28% in Q4 2022.
As you can see, cyber insurance premiums have soared significantly in recent years due to the rising frequency and severity of cyberattacks.
10. Security budget and prevention
Cybersecurity spending rose by 70% over the past four years, according to Moody’s, who also noted that only 8% of the IT budget goes to cybersecurity. That lines up with Vanta’s 2023 “State of Trust” report, which found that 9% of IT budgets are dedicated to security. Meanwhile, the most recent Deloitte survey found that only 6% of security budgets goes to awareness training, which 91% of orgs say they have.
As risk rises and insurance becomes costlier, companies will be forced to spend more money to prevent breaches. They will also likely need to start showing regulators and insurers proof that their security systems are working in order to avoid regulatory penalties and secure good premiums.
The IBM / Ponemon report found that a well trained workforce lowered the cost of breaches by $1.5 million, a 34% difference between companies with good and poor employee training levels. Bottom line, poorly trained workforces cost $5.18 million for a breach, while well trained workforces took a $3.68 million hit (pg. 30).
AI can be used for good and for evil, and investing in AI security tools apparently pays off. Organizations that used Security AI and automation capabilities extensively shortened their time to identify and contain a breach by 108-days and reported $1.76 million lower data breach costs non-users of security AI and automation capabilities.
Phishing in the AI age: Security behavior change training is timeless
While people-targeted attacks may change, the human brain remains the same. Results from a major Hoxhunt study showed that good cybersecurity training protects people against both human and AI-spawned social engineering attacks. The threat of phishing is growing exponentially with the introduction of new tools and techniques, such as AI, QR code phishing, and AitM. A report released by SlashNext Inc. discovered a 1,265% increase in phishing attacks in the 12 months preceding the end of 2023 Q3.
[.c-quote-box][.c-quote-wrapper][.c-quote-icon][.c-quote-icon][.c-quote-right-col][.c-quote-text-wrapper][.c-quote-text]AI lowers the technical barrier to create a convincing picture and impeccable text, not to mention code malware. The threat landscape is shifting incredibly fast now with the introduction of AI to the game. But the good news is that AI can also be used to defend against sophisticated attacks and we’ve seen that good training continues to have a protective effect against AI-generated threats.”[.c-quote-text][.c-quote-text-wrapper][.c-quote-name-wrapper][.c-quote-name]Mika Aalto, co-Founder and CEO of Hoxhunt[.c-quote-name][.c-quote-name-wrapper][.c-quote-right-col][.c-quote-wrapper][.c-quote-box]
Check out how Avanade transformed their risk posture with security awareness and phishing training that measurably changes behavior.







