As QR codes have gained popularity, their use has expanded to include everything from mobile payments to access control and even document sharing. The only problem? Because of their convenience, they easily hide risk.
In a world where no email, text message, or website is safe from cybercriminal activity, it was only a matter of time before QR codes became part of the equation. That's why we factored them into The Hoxhunt Challenge—our most comprehensive test of employee security awareness to date.
Keep reading—or watch the webinar—to learn how it worked and what takeaways we found for those tasked with managing security training programs.
The Hoxhunt Challenge in a nutshell
The Hoxhunt Challenge is a flagship project designed to quantify human cybersecurity risk across the world’s biggest business industries. Launched in September and now complete in time for Cybersecurity Awareness Month, we conducted this test in collaboration with our network of clients around the globe.

Participation in numbers
The benchmark test was executed in 38 participating organizations in nine different industries, operating out of 125 countries worldwide. Collectively, this data set included almost 600,000 employees of varying levels of seniority.
It's just a slice of the bigger picture, but statistically more than enough to draw some meaningful conclusions between various business sectors and their susceptibility for human error-based cyberthreats.
How the Hoxhunt Challenge works
Think of the Hoxhunt Challenge as a regular organizational phishing test on steroids. We wanted to create something broad and comprehensive that delivered honest, probing results of where employees stand today in terms of cyber-resilience. This meant drawing inspiration from what we know to be criminals’ newest strategies and tactics—and incorporating them into the challenge simulations.
22% of phishing attacks used QR codes in October
While a decent portion of internet users know the risks of clicking on a suspicious link or file, few are aware that QR codes can deliver equally nasty payloads. That’s something we took advantage of when designing the simulation, opting to send out real QR codes that, when scanned, would take the participant to a ‘malicious website’.
The tricky thing about QR codes is that although they can be easy to use, they're also proving incredibly easy to abuse. We’ve compiled a significant amount of data showing this phishing strategy is on the rise, and detected in 22% of attacks on our network in the first weeks of October 2023. There’s no better way to get a real sense of how prepared employees are to fend off these attacks than sending them out ourselves.
Pass or fail?
The simulated attack vectors we used in the challenge were sent out to virtually all of the participating organizations’ employees over the last three weeks of September. Recipients had no idea that they were being tested and responded to the training challenge as they would have any other suspicious email.
Responses were divided into three categories:
- Success: Employees identified the attack and reported it with the Hox button in their email browser.
- Miss: Employees neither identified the attack nor reported it with the Hox button but took no action that would give access to confidential data or put their organization at risk.
- Click or scan: Employees didn’t identify the attack and took action that would give access to any confidential data or put their organization at risk.
Engagement rate reflects true human risk
The reason why we decided to create the challenge, and the same concern we had when we built our products, is the undeniable relationship between engagement and risk in business cybersecurity.
It’s become particularly relevant in the post-pandemic world as many companies decide to permanently adopt the hybrid or completely remote working models that staff love. Cybercriminals are happy to capitalize on this shift by targeting workers in many new and creative ways.
Yet, as one side of the fight for data ownership advances, most businesses remain unchanged in their cybersecurity practices. In many cases, remote teams are actually less prepared to handle threats than they would be in an office, as participation in security initiatives isn't the same.
Even in physical settings, it's clear that engagement makes a huge difference. Anyone who’s managed a team can anecdotally say that their IT staff and users alike are more likely to stay up-to-date on security protocols and patching when they care about the success of the company. Security measures become part of their day-to-day rather than a foreign concept that must be handled by a separate team.
With so many evolving standards and changes in the way business is done, our goal with the challenge was to find tangible evidence for what we’ve been saying for so long: employee engagement has a clear link with human cybersecurity risk levels.
The ideal outcome? Getting leaders to recognize that employees are the last, but most important, line of defense in any cybersecurity strategy and they should invest accordingly.
Global insights
Broadly, one could argue that the results of the challenge paint a dark picture of the state of employee security awareness globally.

The data shows that overall, just over one-third (36%) of recipients successfully identified and reported the attack with the Hox button. More than half failed to recognize it as a threat, while another 5% of employees actually scanned the QR code or clicked a link.
Put into real-world context that would mean that a majority of organizations would be left vulnerable, if not completely compromised, by a similar phishing attack.
Retail companies missed the simulation the most
The Hoxhunt Challenge revealed some interesting insights into how employees in different industries and job functions dealt with the simulated attack. We saw a significant difference between industry performance, with manufacturing having a 1.6x higher fail rate than other industries.

The retail industry had the largest miss rate by far, where only 2/10 employees and organizations engaged with the benchmark.
Leading the pack’s positive results were organizations in legal and business services. Attribute it to their direct contact with clients or to the important role HR and security teams play in their business, but staff in this sector successfully reported the suspicious QR code 1.5x more than any of the others tested.
It's worth emphasizing that this is a very general look at how phishing awareness is currently standing in these industries. Individual organizations may have vastly different results, likely depending on the state of their security training and education systems.
Yet, at the same time, it's interesting to note the trends between different business verticals. Perhaps they say something about the level of digital risk literacy in each, or it could just be a sign of the divide between ‘tech-savvy’ and ‘less tech-savvy’ organizations.
Employees in communication positions clicked or scanned the simulation the most
Delving deeper into groups of people, we were curious to find out whether an employee’s job function had an impact on their ability to spot a suspicious QR code. It turns out that, in most cases, it did.

The glaring finding of all the job function data we collected is how underprepared communications staff seem to be with respect to identifying and acting on potential phishing attacks. They engaged with the QR code 1.6x more than any other job function.
Most of the others averaged between factors of 0.8 to 1.2, although Human Resources teams placed closely behind communications at a click/scan rate of 1.3.
Again, setting an example for everyone else were employees with legal responsibilities, who came out on top with an average factor of only 0.4.
Sales employees proved the most likely to miss a potential attack, with 32% of test recipients failing to take action with the Hox button.
The cybersecurity human risk benchmark’s main findings
There’s an extensive amount of data to go through when it comes to understanding how employees react to potential phishing attacks. Our main findings, however, are summed up in a few key points:
1. Engaged employees reduce human risk
Employee engagement is defined as the extent to which employees feel passionate about their jobs, are committed to the organization and its goals, and are motivated to contribute their best work.
During the challenge, we quickly discovered a link between staff engagement levels and cybersecurity readiness. Individuals who weren't actively invested in their job responsibilities and the organization as a whole had a miss rate of 90%, meaning they were unable to correctly identify phishing emails nine out of ten times. On the other hand, employees who were engaged with their work had a miss rate of only 40%.
That decrease of more than half is a stark contrast and indicates that engaged employees have a significantly greater understanding of their organization’s cybersecurity policies.

2. Onboarded employees are more vigilant
Just like any other aspect of a job, the challenge clearly illustrated the positive difference proper onboarding can make in mitigating human cyber-risk.
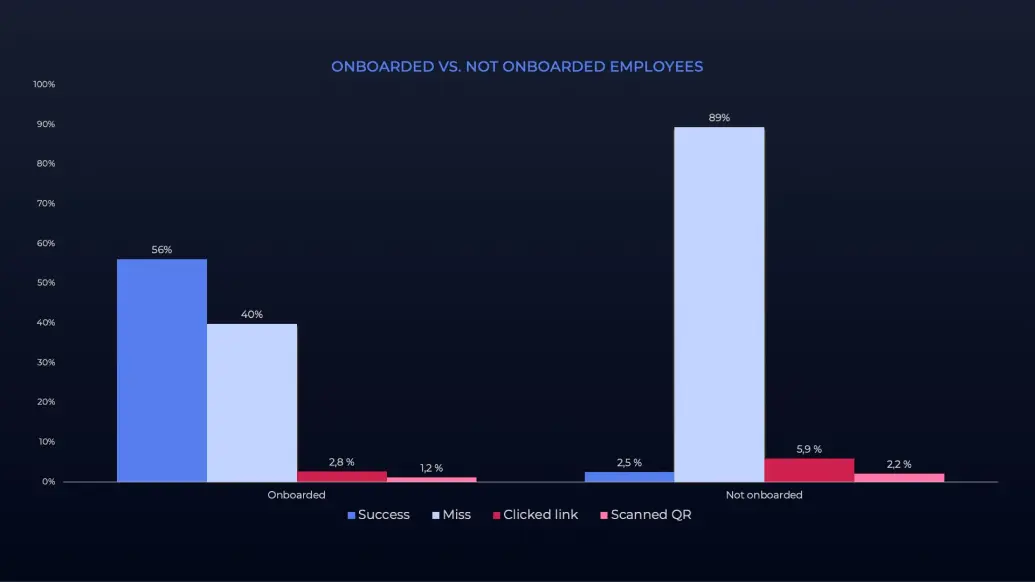
New employees who completed the onboarding process and received pre-training had much more vigilance in identifying phishing emails than those who did not. They felt better positioned to assess the potential threats in front of them and report questionable emails with confidence.
This proves that the onboarding process isn't just a formality. It's an incredibly important part of ensuring that teams are ready to mitigate the various risks and vulnerabilities that come with doing business digitally.
3. Active employees are more resilient
The biggest overarching lesson we’ve learned from this year’s Hoxhunt Challenge is that active employees are about 14x better than those who aren’t active. That’s the factor by which the former group reported QR code attacks compared to their counterparts.
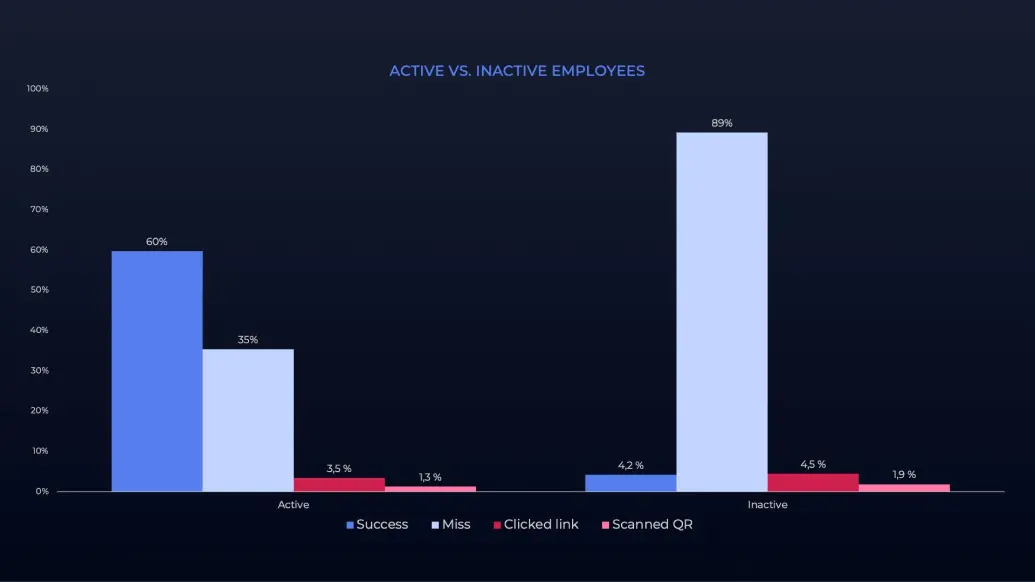
Individuals with a vested interest in their organization’s day-to-day affairs simply paid more attention to what was coming into their inboxes. Additionally, active employees had the cyber judgement to avoid scanning the code altogether and failed less by a margin of roughly 25%.
4. Long-term training improves performance
Even after onboarding and several successful years on the team, no employee will be as by-the-book as they were when they first started. The harsh reality is that any one of an organization’s staff members—regardless of their position, experience level, or formal education—can fall for an attack. It again ties back to the importance of conducting training regularly, ideally just as committedly as any type of customer service standards program or performance review.
Our analysis shows that longer-term training also helps improve performance over time. Those who participated over a period of 18 months scored better than those who had only trained for a short amount of time. Further, experienced employees reported the suspicious QR code three times more than employees new to the training.
This insight shows that cybersecurity training shouldn't be a one-off event. If employees are regularly trained, they will become more aware of potential threats, learn to spot anomalies faster, and have better defenses in place to protect the organization’s data and assets.

The best recommendation we can give any company looking to improve its cybersecurity posture is to invest in ongoing training. This should include both initial onboarding and refresher courses that are provided regularly to ensure employees are kept up-to-date on the latest threats, vulnerabilities, and best practices. The frequency of these sessions might change depending on the organization’s risk profile but should generally be conducted at least every six months.
Continuous training matters
The takeaway from the Hoxhunt Challenge we can confidently give anyone who’s failed to read the above article is this: continuous training matters. Businesses today are just as susceptible, if not more so, to digital risks as they are to real-world ones.
It only makes sense to prepare employees with the relevant skills, knowledge, and practice that they’ll undoubtedly need on the job. Failing to provide it promotes a reality of increased risk where organizational data is more of a liability than anything else.
About the author
Eliott is a Product Marketer passionate about taking innovative products to the market. He enjoys finding insights and opportunities from numbers and spinning them into captivating narratives.
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt







