What is QR code phishing (quishing)?
QR code phishing - “quishing” - is a social-engineering attack where a malicious QR code lures you to a spoofed site or malware download. It’s potent because scans happen on mobile, outside email defenses, and URLs are harder to inspect. Defend by teaching pause-verify-report, enforcing MFA, and running QR sticker simulations to test real-world behavior.
QR code phishing at a glance
- Goal: steal credentials/MFA tokens or trigger malware via a scan.
- Where it appears: emails, posters, menus, parcels, parking meters, event signage.
- Why it works: mobile UX hides full URLs; physical context feels trusted; email filters can’t see the final mobile action.
- Fast defenses: MFA, domain allow/deny controls, clear reporting route, and physical simulations to expose risky habits.
How a typical quishing flow works
- Attacker plants a QR (in an email image or over a legitimate poster).
- User scans → redirected to fake login or malware page.
- Credential harvest or device compromise occurs.
- Incident expands unless the user reports early and credentials are reset.
Note: The term ‘quishing’ is often considered somewhat controversial since QR code phishing is a variation on the payload type, as opposed to terms like phishing/vishing/smishing - which are all variations on the vector delivery method.
How does QR code phishing work?
Attackers place a malicious QR code in email or the physical world. When scanned, the code opens a spoofed login or malware page on mobile - outside email filters - often using URL shorteners and look-alike domains. Victims enter credentials or approve MFA.
The attacker's quishing playbook
Lure creation: Static or dynamic QR encodes a hostile URL; tracking parameters help attackers test and iterate.
Delivery:
- Email: PNG/JPG QR in “delivery notice,” “voice message,” or “MFA reset.”
- Physical: Overlay sticker on posters/menus, lobby kiosks, parking/pay stations.
Redirect & cloak: URL shorteners, HTTPS padlocks, and look-alike domains hide risk; pages often mimic Microsoft/Google or payment portals.
Capture or compromise:
- Credential harvest/MFA bypass (e.g., session token theft).
- Malware via drive-by or sideload prompts.
Exploit & persist: Attackers pivot to inbox rules, payroll changes, or vendor fraud.
Common vectors and quick defenses
Why it evades traditional defenses
- The decisive click happens on mobile, not inside the email client - so link rewriting and sandboxing miss it.
- Shortened URLs + tiny mobile address bars obscure domains.
- Dynamic QR lets attackers rotate destinations post-distribution.
What to look for (user coaching)
- Off-brand domains, extra subdomains, or typosquats.
- Login prompts after scanning a poster/menu - unnatural context.
- Pages asking for MFA codes, recovery answers, or payment details.
Further reading (authoritative guidance)
- FTC: QR-code scam alerts
- U.S. Postal Inspection Service: Quishing alert
- NCSC (UK): Phishing guidance
- ACSC (Australia): Quishing overview
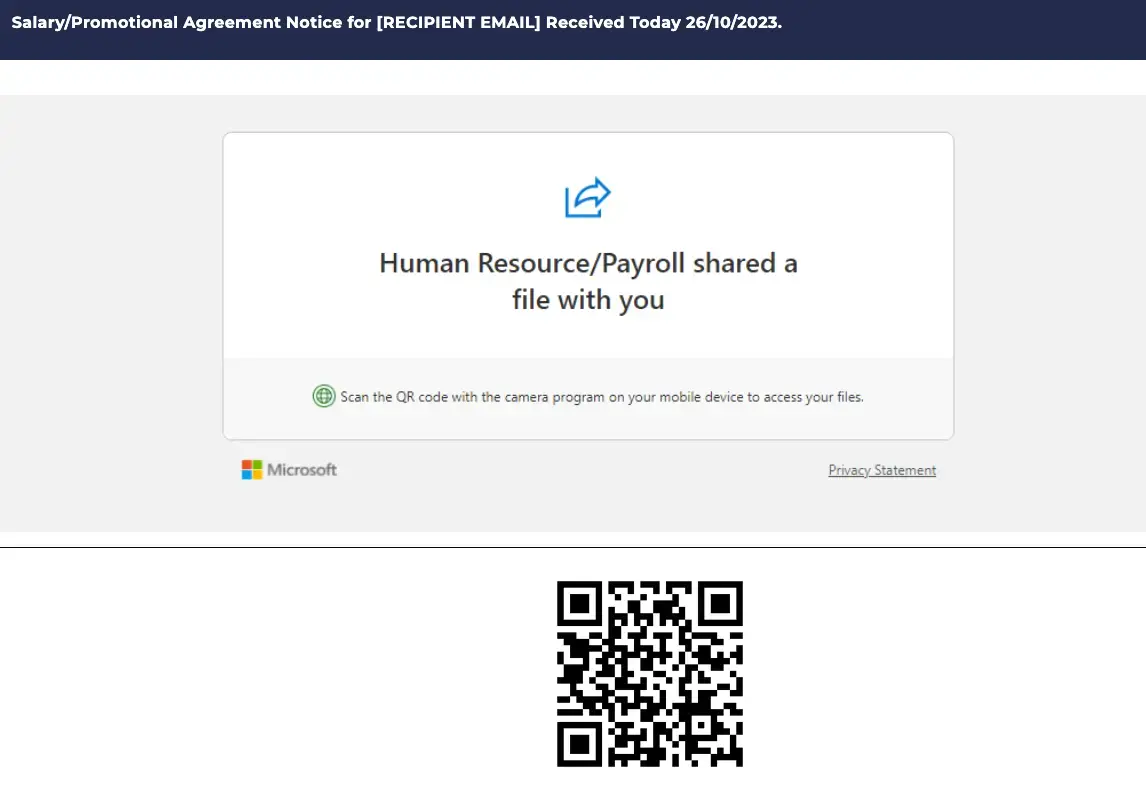
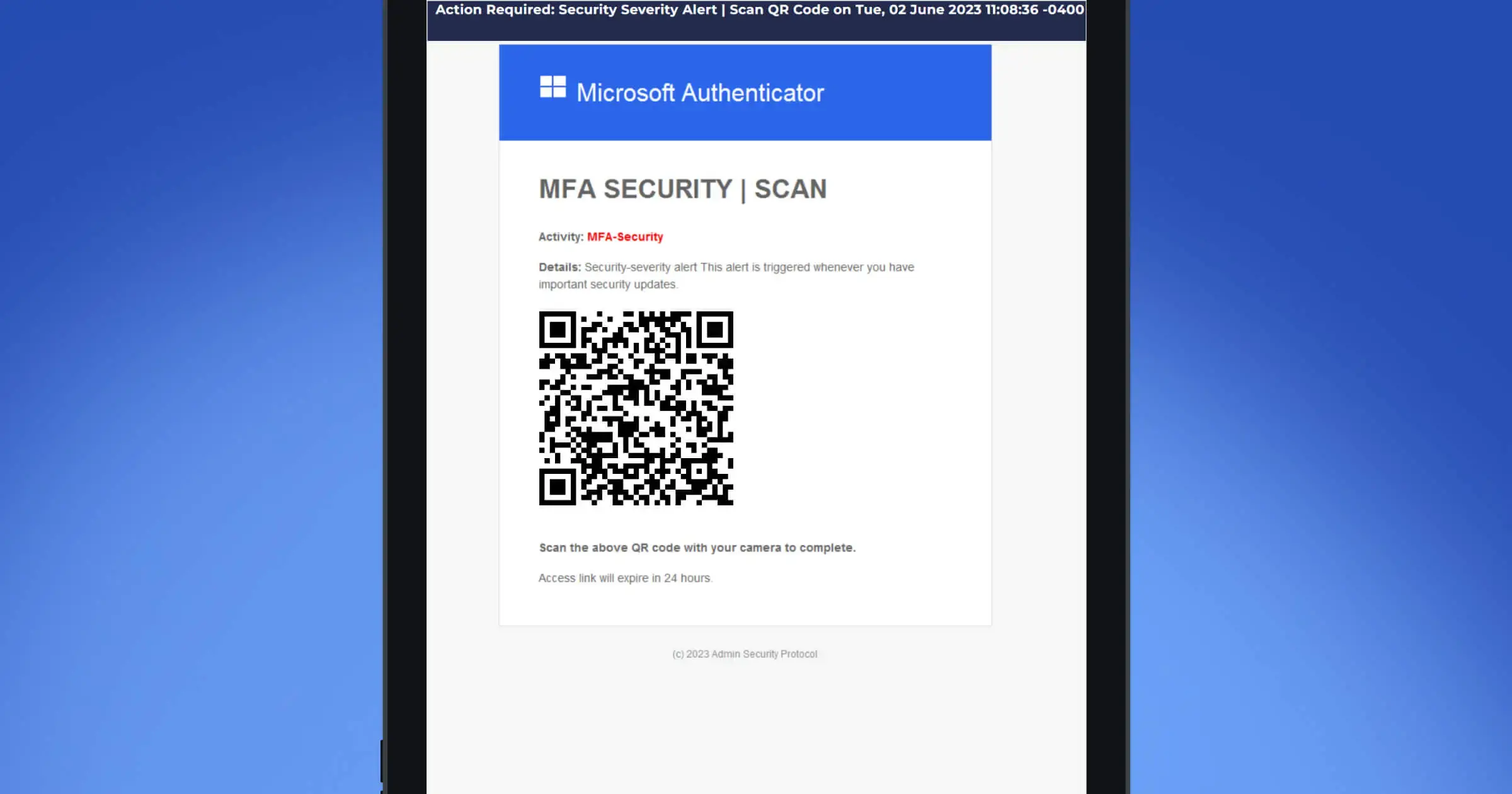
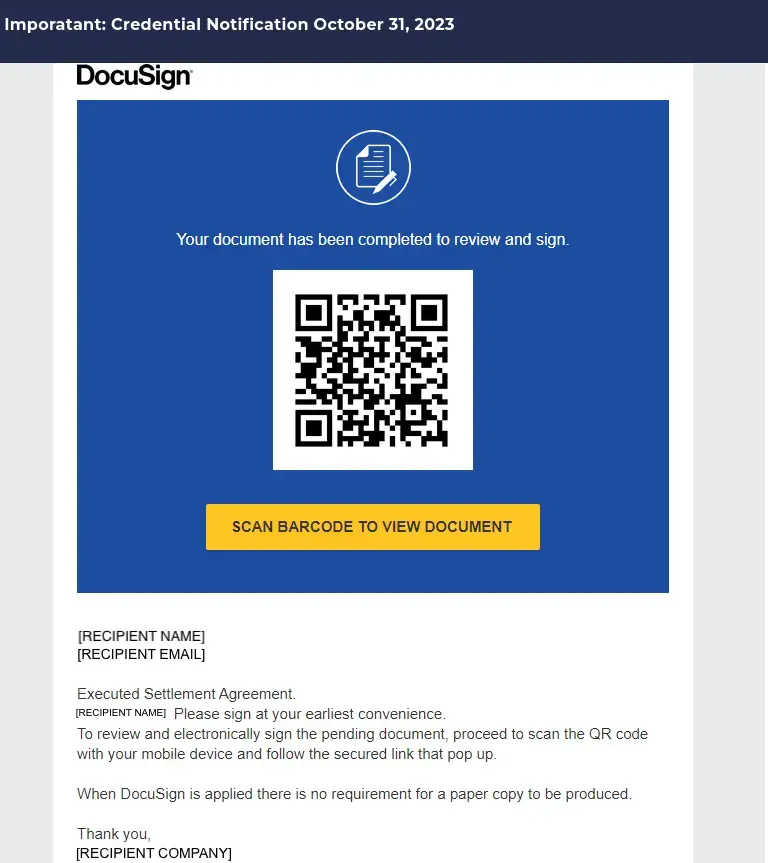
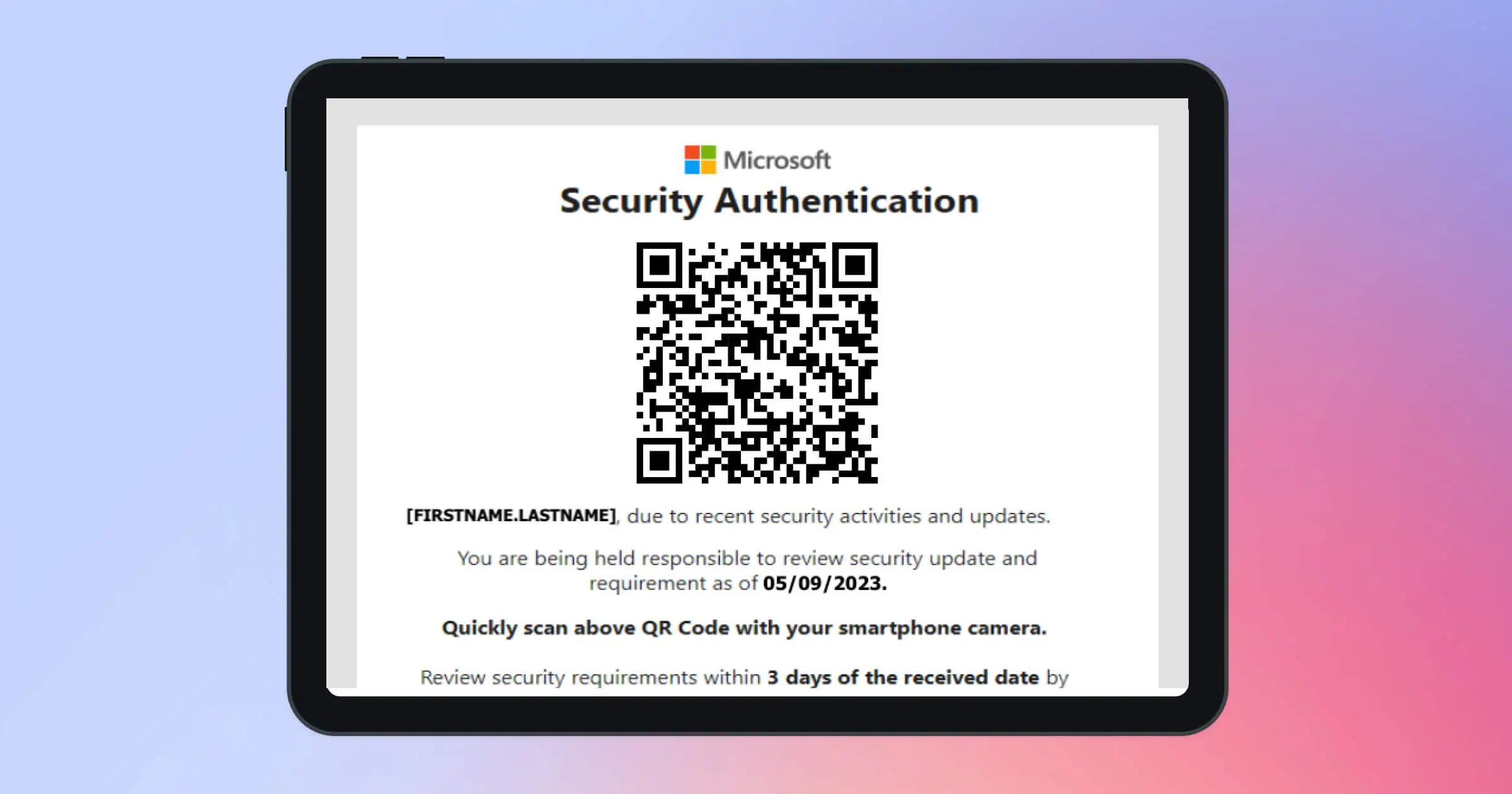
Real-world QR scam patterns our team observed
Here are some common quishing patterns we’ve seen: payroll/file shares, invoice/payment notices, MFA prompts, e-signature requests, generic “security updates,” and parcel deliveries. Each uses a QR to push you to a spoofed login or payment page. Train people to spot red flags and use the official app/site or the reporting button instead.
How to simulate a QR-phishing attack with stickers (step-by-step)
Run a QR-sticker simulation to test real behavior at the scan point. Place bold “DON’T SCAN!” stickers in high-traffic areas, drive scans to a safe landing page, and debrief with micro-lessons. Keep it ethical, short, and measurable - optimize for reporting rate and time-to-report, not clicks.
Step 1: Decide your approach
You’ve got two paths:
- Quick start: Use our ready-made sticker design that points to a non-personalized landing page.
- Full custom: Create your own sticker and landing page, aligned with your brand and voice.
Both work - the question is whether speed or customization matters more for you.
Step 2: Set your objectives
Ask yourself:
- Do I want employees to notice the QR code but resist scanning?
- Or do I want them to scan and land on an educational page?
- What will success look like - scan rates, survey results, conversations sparked?
E.ON found that 70% of employees noticed the stickers but didn’t scan them - and that was the win. People had learned the core lesson: think before you scan.
Step 3: Design your sticker
The sticker is the hook.
E.ON used “DON’T SCAN!” as the headline - provocative enough to grab attention, but not so aggressive that it felt like a trap.
Tips for your design:
- Keep it bold and visible.
- Use a short message (“Don’t scan” / “Pause before scanning”).
- Make sure the QR code itself is central - tempting, but suspicious.
Step 4: Build the landing page
If you go custom, your landing page is the payoff. When someone scans, they should quickly learn:
- Why QR codes can be risky.
- How criminals disguise them.
- Simple steps to stay safe.
Keep it mobile-friendly (everyone is scanning on their phone), and consider adding a quick quiz or checklist to make it stick.
Step 5: Launch in the wild
Now it’s time to print and place your stickers. Think about high-traffic spots: cafeterias, entrances, elevators, break rooms.
Communicate just enough beforehand - so employees know this is an awareness initiative, not a prank - but keep some surprise to spark curiosity.
E.ON paired their campaign with an intranet article revealing the story behind the stickers, which became one of their most-read posts.
Step 6: Measure and learn
Don’t let the campaign end at sticker removal. Collect feedback and data:
- Did employees notice the QR codes?
- Did they scan - or report?
- What did they take away?
- What conversations did it spark in teams?
The answers will help you refine your next campaign and show leadership that physical awareness tactics can have real impact.
Why it works
QR code campaigns stand out because they bring security awareness into employees’ daily environment. They spark curiosity, discussion, and reflection - things a slide deck rarely does.
And as E.ON proved, the goal isn’t clicks for the sake of clicks. Sometimes the best result is people not scanning - because that’s exactly the behavior we want in the real world.
👉 Ready to try it? Start small with our provided sticker and shared landing page, or go big with your own design. Either way, you’ll be putting security top-of-mind where employees least expect it - and that’s what makes it powerful.
Where should you place QR-sticker simulations for maximum impact?
Place QR-sticker simulations where people naturally scan or move quickly: building entrances, elevators, printers/copiers, cafeterias, reception, meeting rooms, parking/pay stations, and event booths. Add a few remote/home spots (home printers, parcel areas). Coordinate with Facilities for safe placement, avoid brand damage, and include clear reporting instructions.
High-yield placements (by behavior)
- Entrances & reception: Captures most foot traffic; pairs well with a short intranet post.
- Elevators & corridors: Idle time = curiosity; great for “Pause before scanning” headlines.
- Printers/copiers & mailrooms: Natural document workflows; tie to “scan-to-view” lures.
- Cafeterias & break areas: Low-stakes environment; high conversation spillover.
- Meeting rooms & hot-desks: QR menus/room tech make this a realistic context.
- Parking meters & pay stations: Mirrors real-world payment scams; keep signage unobtrusive.
- Events & booths (internal/external): Check-in, Wi-Fi, promos - prime for look-alike domains.
- Remote/home setups: Home printers, parcel drop zones, shared family tablets.
Do / don’t (quick guardrails)
- Do: Get Facilities sign-off; use removable adhesive; place at eye level; add a tiny footer with “verify via official app/site - report suspicious codes.”
- Don’t: Cover legal signage, company logos, safety notices, or customer-facing materials; avoid sensitive areas (HR interview rooms, medical spaces).
Quishing prevention best practices (organization-level)
Reduce QR code phishing attacks by pairing mobile-first user coaching with layered security measures. Standardize pause-verify-report on mobile devices, enforce strong multi-factor authentication, harden domains/SSO, and tune email security tools for QR lures in phishing emails. Run periodic QR-sticker simulations in public spaces to build habits, then track reporting rate and time-to-report.
1) Make “pause-verify-report” the default on mobile
- Pin your report button in iOS/Android mail; teach users to avoid scanning code images from unsolicited emails or social media.
- Coach the smell test: if a QR leads to login credentials, payment methods, or bank details, stop and report.
- Emphasize official channels (apps/bookmarks) over ad-hoc scans from unknown sources.
2) Harden identity & access (limit credential harvesting)
- Enforce MFA with phishing-resistant options (security keys/passkeys) for company login credentials.
- Restrict risky mobile SSO flows; alert on unexpected authentication notifications and session anomalies.
- Auto-revoke tokens on suspected credential theft; require re-auth on sensitive actions.
3) Tune email security for QR-based lures
- Update detections for QR code images (two-dimensional barcodes) and dynamic QR codes embedded in phishing campaigns.
- Add banner hints for “scan this QR to view invoice/voice message.”
- Use cloud email security providers or SEG add-ons to correlate links in emails with mobile outcomes.
4) Control destination risk (web & DNS)
- Block known malicious websites and fraudulent websites; add advanced DNS security and safe-browsing controls on mobile.
- Watch for look-alike domains targeting payment processing and data entry landing pages; monitor brand abuse.
- Quarantine malicious software downloads and suspicious code scanning apps/barcode scanners.
5) Run realistic training - short, frequent, ethical
- Ship QR-sticker simulations in physical locations (reception, printers, cafeterias) to replicate traditional phishing tactics in the real world.
- Keep it learning-over-punishment: instant teach-back, micro-lessons, and a visible reporting route.
- Rotate lures (invoice, MFA, delivery, Adobe Acrobat Sign, event Wi-Fi) to match current threat actors.
6) Instrument and iterate like a product
- Prefer dynamic codes for placement analytics; use UTMs per location and segment (finance, IT, managerial roles, consumer-facing roles).
- Track reporting rate, time-to-report, resist vs. scan, and downstream reductions in visits to malicious sites.
- Share a quarterly email security report to stakeholders; align with business continuity and cybersecurity policies.
7) Guard high-risk workflows
- Payment & finance: require official portals; block direct QR access to bank account credentials, credit and debit card numbers, and invoices.
- Field & events: standardize codes for signs, event posters, and tickets; pre-approve code placements and code creators.
- Logistics: validate USPS delivery and courier notices via apps - never by scanning stickers on doors.
Quick checklist (copy/paste)
What does Hoxhunt’s Human Risk Benchmark reveal about QR risks?
Our Human Risk Benchmark - spanning 21M+ simulations and 2M+ users in 125 countries - shows behavior-first programs lift real outcomes: users become ~6× less likely to click and ~7× more likely to report suspicious content, cutting exposure to malicious links and fake websites.
Key takeaways you can apply today
- Moment-of-risk beats reminders: Simulations at real physical locations (printers, reception, events) create stronger habits than generic emails about phishing attempts.
- Reporting is the north star: Optimize reporting rate and time-to-report; they correlate with drops in visits to malicious sites and spoof logins requesting company login credentials.
- Role-based exposure: Finance, IT, field and consumer-facing teams see more payment processing and invoice lures - prioritize sticker placements and follow-ups here.
- Mobile-first reality: Most code phishing attacks end on a phone; coach users to avoid scanning from unsolicited emails or social media and to verify via official apps/bookmarks.
- Layered controls matter: Combine MFA (security keys/passkeys), email security tools (QR-lure detections), and advanced DNS security to blunt threat actors exploiting dynamic QR codes.
Turn insights into a QR program
- Pair each sticker with a matching lure theme.
- Use dynamic codes + UTMs to segment by site/department; ship a monthly email security report.
- After scans or reports, deliver a 60-second micro-lesson on spotting suspicious links and fraudulent websites.
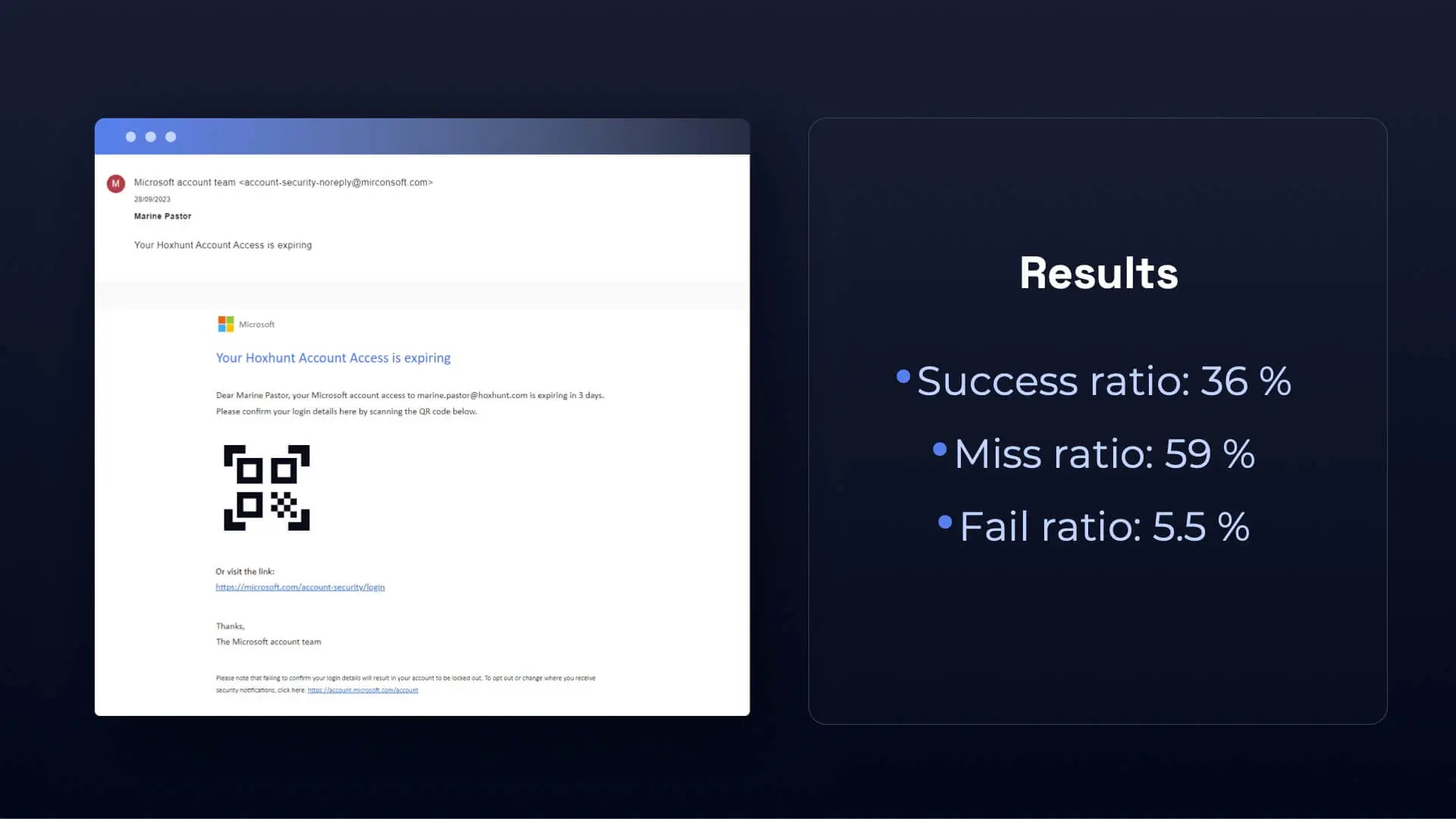
About Hoxhunt
Hoxhunt helps organizations reduce human cyber risk with behavior-first training, real-threat reporting, and adaptive simulations - including QR-phishing (quishing) scenarios in physical locations.
We nudge safer habitse, reinforce them with micro-lessons, and prove impact with metrics that show real behavior change.
Why teams use Hoxhunt
- Drive next-level employee engagement: Enhance the impact of your training by tailoring it to every employee’s role, department, location, and more to ensure your message resonates.
- Maximize results with minimal effort: Do more than just meet compliance. Boost participation with engaging training and build a foundation of security-first practices on autopilot.
- Create a positive security culture: Encourage secure behaviors with gamified awareness and micro-trainings that minimize disruption and proactively fill in their skill gaps.
Below you can see what Hoxhunt simulations look like for your end users.
FAQ: Quishing & QR-sticker simulations
Do QR-sticker simulations “trick” people?
No. They’re education-first. You announce the program broadly (or immediately debrief), avoid sensitive contexts, and provide instant guidance and a reporting route. The goal is habit change, not gotchas.
How often should we run them?
Quarterly is a good cadence. Rotate locations and lures (invoice, MFA, delivery, e-signature) to avoid banner-blindness. Tie each run to a 60-second micro-lesson and a reporting reminder.
What happens if someone scans?
Send to a safe landing page that explains quishing risks, shows the red flags they missed, and links to the official app/site and the report button. Optional: a one-question quiz to reinforce learning.
Legal/brand considerations?
Avoid customer-facing spaces and regulated/sensitive areas (HR interview rooms, medical spaces). Don’t cover legal/safety signage. Keep copy neutral (“Pause before scanning”). Provide clear opt-out and a contact for questions.
What should the reporting route be?
A one-tap button in mobile mail (or Slack/Teams shortcut). Make it visible everywhere you mention QR safety and include it on the landing page after any scan.
Sources
Internet Organised Crime Threat Assessment (IOCTA) 2024 - Europol
Phishing - ENISA (European Union Agency for Cybersecurity)
Scammers hide harmful links in QR codes to steal your information - FTC
“Quishing” (QR code phishing) - U.S. Postal Inspection Service
Phishing: Respond & Recover - NCSC
Quishing (QR code phishing) - Australian Cyber Security Centre (ACSC)
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt