Office 365 credential phishing attacks are one of the most common phishing attacks that we see every day. The vast majority of these attacks are very poorly made. These so-called lazy attacks could come from strange email addresses with obviously suspicious content. These are the type of emails that blind people from the exceptionally crafted phishing emails.Perhaps many of us thought before that recognizing an attack is easy – who needs training for that? We will show you how wrong this mindset is. When attacks are unusually good, many of us could fall victim.
Examples of lazy Office 365 phishing attacks

The two emails above are good examples of the level of the most common O365 phishing attacks. Even a slightly educated person in cybersecurity can quickly figure out that these are not legit and should be left alone. However, sometimes we make errors, or our curiosity drives us to check what’s behind the email. The most simple O365 phishing attacks often take the victims to a poorly done landing page too:

A poor landing page is typically (“Office login pages”) built on Google/Microsoft forms, Excel, and other Office tools.
So are these Office 365 phishing attacks dangerous?
Absolutely. Since the vast majority of O365 attacks look like the ones above, people may start to believe that they can instantly spot every phishing email. Hoxhunt end-users commonly leave feedback that our simulations are too complicated - that even real phishing attacks are not that hard.But in reality - if these poor ones make the most substantial portion of O365 attacks, the rest is difficult even for cybersecurity professionals to spot. The poor ones will make you think that you know what you are doing, and you won’t be fooled. Staying alert is necessary – and practicing with challenging simulations is vital.
What does an exceptional Office 365 credential phishing attack look like?
Some of the best O365 phishing attacks are more or less straight copies of real Microsoft emails. Teams messages, email server notifications, O365 subscriptions. Here are two examples of great ones below:
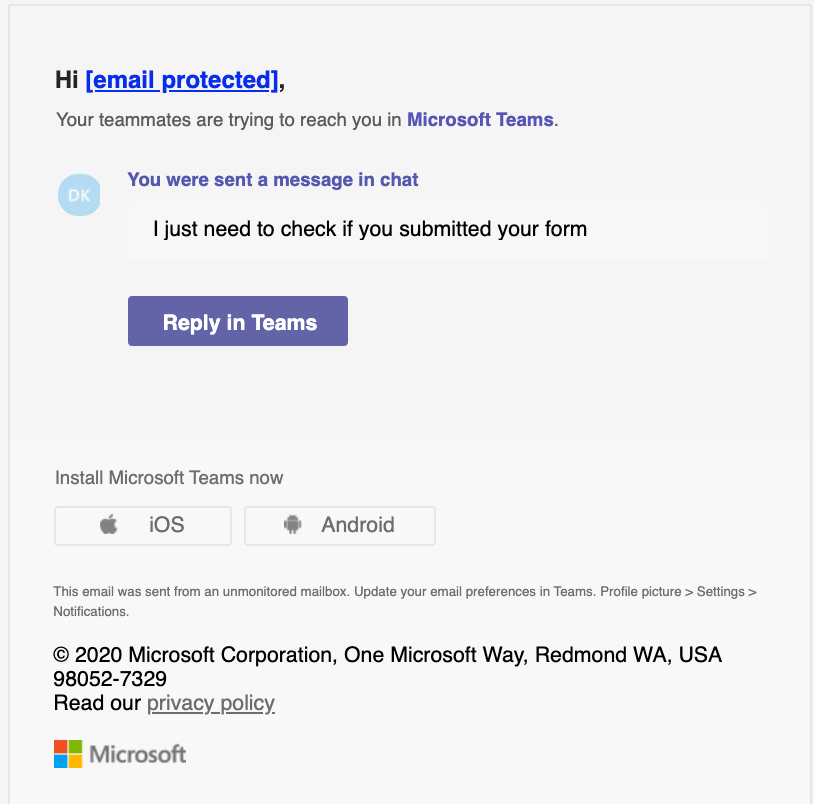
Phishing using Microsoft Teams look-alike message.

O365 subscription renewal phishing email. These challenging phishing attacks are accurate and realistic copies of real Microsoft emails. Besides, their sender addresses are also commonly spoofed well. The receiver sees that the sender is, for example, ´[email protected]´, while it was sent from another email address. In the worst-case, these well-crafted phishing emails take the victim to an authentic-looking copy of the Microsoft login page. Watch the video to see how it works.[embed]https://youtu.be/vPR0aul__8E[/embed]This fake Microsoft page looks almost identical to the real one, and it even features all the same animations. This page fetches your organization’s own Microsoft login page. If you press “Sign in” it redirects you to the real Microsoft website to which you are probably already signed in, so you will never know that you just gave your credentials to a fisherman. In this case, to avoid being phished, the only way to tell that this site is fake is to look at the URL.







